Premium Only Content
Chapter-17, LEC-4 | Downloading Files | #ethicalhacking #cybersport #cybersecurity
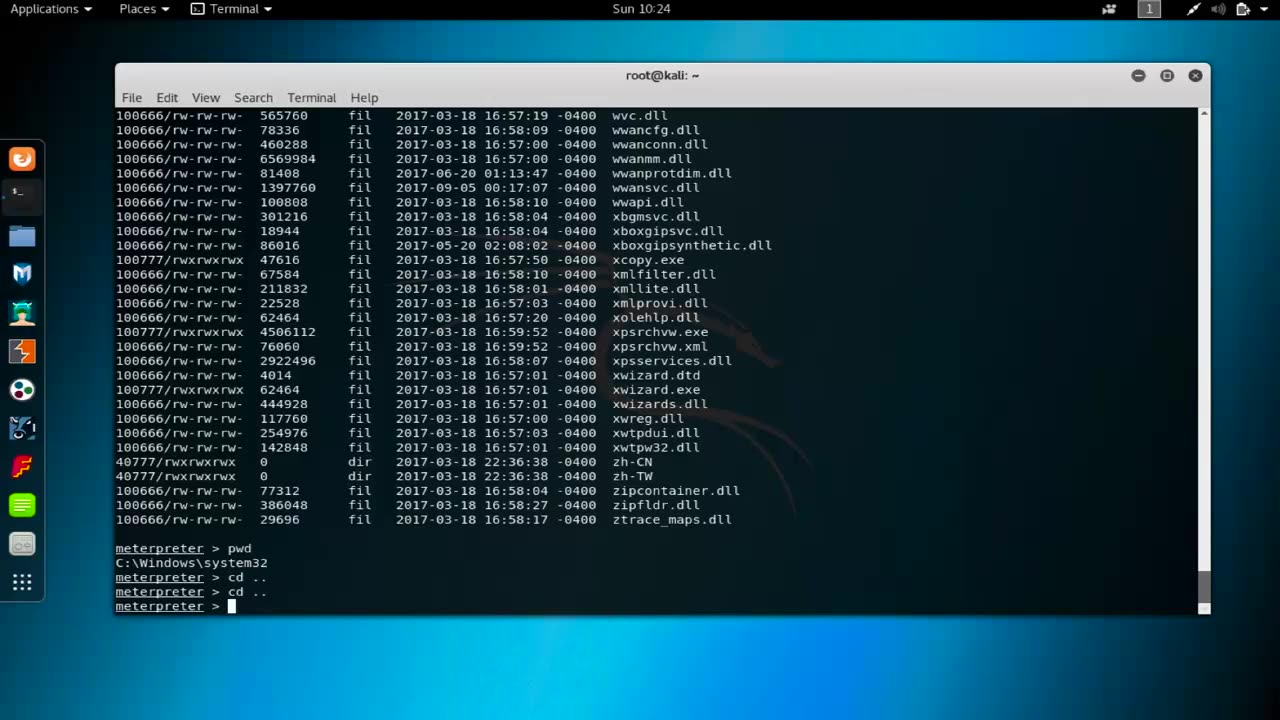
Downloading files is a common post-hacking session technique that is used to extract sensitive data or other valuable information from a compromised system or network. This technique is often used by attackers to exfiltrate stolen data or to download additional tools or payloads onto the compromised system.
When an attacker gains access to a system using a Meterpreter payload or other post-exploitation tool, they can use various techniques to download files from the compromised system. For example, they can use the "download" command in Meterpreter to transfer specific files or folders to the attacker's machine. Alternatively, they can use other tools, such as FTP or SCP, to copy files to a remote server or cloud storage service.
Downloading files can be a time-consuming process, especially if the target system contains large amounts of data. To speed up the process, attackers may use compression tools like "tar" or "zip" to bundle multiple files or folders together and transfer them in a single archive. They may also use network-level techniques like port-forwarding or VPNs to bypass firewalls or other security measures that may block the transfer of files.
Downloading files can be a risky post-hacking session technique because it leaves traces of the attacker's activities on the compromised system, making it easier for security teams to detect and investigate the breach. As such, attackers may use various tactics to obfuscate their activities, such as deleting logs or using encryption to hide the data that is being exfiltrated.
Overall, downloading files is a powerful post-hacking session technique that can allow attackers to exfiltrate sensitive data or download additional tools or payloads onto the compromised system. However, it is also a high-risk technique that requires careful planning and execution to avoid detection and ensure a successful breach.
-
 3:09:52
3:09:52
Right Side Broadcasting Network
4 hours agoLIVE REPLAY: White House Press Secretary Karoline Leavitt Holds a Press Briefing - 11/4/25
27K6 -
 1:58:04
1:58:04
The Charlie Kirk Show
2 hours agoGo Vote! + Healthcare and the Shutdown | Dr. Oz, Baris | 11.4.2025
29K3 -
 58:49
58:49
The White House
3 hours agoPress Secretary Karoline Leavitt Briefs Members of the Media, Nov. 4, 2025
3.36K5 -
 1:00:22
1:00:22
Sean Unpaved
2 hours agoCarousel Chaos: CFB Week 10 Shocks & Drops, Cardinals Stun MNF, & CBB's Opening Tip-Off Frenzy
6.74K1 -
 1:57:43
1:57:43
Steven Crowder
4 hours agoFailed Hit Job: Another Trump Media Hoax Exposed
274K232 -
 56:36
56:36
The Rubin Report
3 hours agoFox Hosts Stunned by Piers Morgan’s Dark Prediction for NYC Under Zohran Mamdan
25.4K37 -
![GRAY ZONE DEVLOG FOR .3.5 UPDATE!!! [RGMT CONTENT Mgr. | RGMT GL | GZW CL]](https://1a-1791.com/video/fww1/11/s8/1/0/K/B/w/0KBwz.0kob-small-GRAY-ZONE-DEVLOG-FOR-.3.5-U.jpg) LIVE
LIVE
XDDX_HiTower
2 hours ago $0.61 earnedGRAY ZONE DEVLOG FOR .3.5 UPDATE!!! [RGMT CONTENT Mgr. | RGMT GL | GZW CL]
82 watching -
 LIVE
LIVE
LFA TV
16 hours agoLIVE & BREAKING NEWS! | TUESDAY 11/4/25
2,477 watching -
 DVR
DVR
The Shannon Joy Show
3 hours agoICE Brutality In Evanston, Illinois Sparks New Outrage * GOP Seeks New FISA Re-Authorization * Are Tucker Carlson & Nick Fuentes Feds?
15.4K4 -
 1:41:24
1:41:24
The Mel K Show
3 hours agoA Republic if You Can Keep It-Americans Must Choose 11-04-25
20.8K1