Premium Only Content
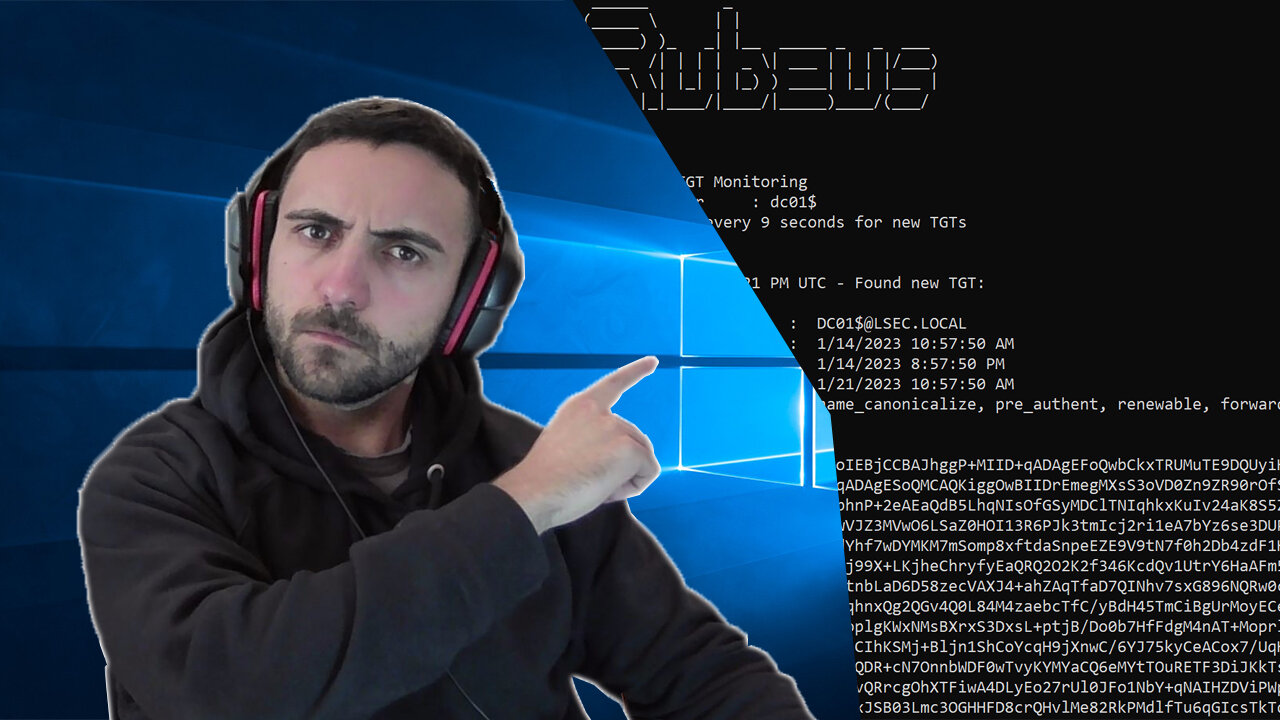
Unleashing the Power of Unconstrained Delegation: A Step-by-Step Tutorial
Delegation is a powerful feature in Active Directory, but it can also be a major security vulnerability if not configured properly. In this tutorial, we will show you step-by-step how to identify and exploit unconstrained delegation vulnerabilities in your Active Directory environment. We will cover the basics of how unconstrained delegation works, the potential risks, and how to use tools to detect and exploit these vulnerabilities.
JOIN MY DISCORD TO SHARE KNOWLEDGE AND EXPERIENCE
---------------------------------------------------
https://discord.gg/dWCe5ZMvtQ
LINKS
---------------------------------------------------
SpoolSample: https://github.com/leechristensen/SpoolSample
Ghostpack Precompiled Binaries: https://github.com/r3motecontrol/Ghostpack-CompiledBinaries
FOLLOW ME
---------------------------------------------------
Twitter: https://twitter.com/lsecqt
Twitch: https://www.twitch.tv/lsecqt
Reddit: https://www.reddit.com/user/lsecqt
Medium: https://medium.com/@lsecqt
Support my Work: https://www.buymeacoffee.com/lsecqt
TIMESTAMPS
--------------------------------------------------
00:00 - Intro
00:25 - Configuring Client Side
01:37 - Configuring Server Side
02:38 - Enumeration and Exploitation
06:03 - Patch ideas
06:45 - Outro
red teaming 101
red team 101
red team
red teaming
hacking
ethical hacking
unconstrained delegation
kerberos delegation
kerberos exploit
delegation exploit
purple teaming
etw bypass
event tracing for windows
even tracing for windows bypass
etw
C2
hack discord
reverse shell
red teaming guide
hacking guide
red teaming tutorial
hacking tutorial
c2
command and control
hacking with discord
hacking c2
-
 LIVE
LIVE
Rebel News
51 minutes agoConvoy punishments, Alberta vs BC Indigenous projects, Carney's body language | Buffalo Roundtable
302 watching -
 1:58:38
1:58:38
Steven Crowder
4 hours agoPillaging America: Lefty Celebs Prove Exactly Why Every Illegal Must Get Out
221K183 -
 LIVE
LIVE
Tim Young
1 hour agoShutdown Special LIVE w/ 19 members of Congress! Powered by @Kalshi
101 watching -
 1:05:29
1:05:29
The Rubin Report
2 hours agoFight Over Trump Lies Gets so Ugly It Could Be Eric Trump’s Final Appearance on This Show
35.4K36 -
 1:32:12
1:32:12
Nikko Ortiz
3 hours agoRealistic COP Simulator | Rumble LIVE
14.5K -
 LIVE
LIVE
LFA TV
14 hours agoLIVE & BREAKING NEWS! | WEDNESDAY 10/8/25
3,931 watching -

The Mel K Show
2 hours agoMORNINGS WITH MEL K -Lobbyists and Greed have Replaced the Will of We the People 10-8-25
16.4K11 -
 LIVE
LIVE
The Shannon Joy Show
1 hour agoGold Surge Persists Signaling Recession, More Inflation & Potential War - Live W/ Peter Schiff!
206 watching -
 1:03:42
1:03:42
Grant Stinchfield
2 hours agoThe People Have Spoken: Trump Rising, Democrats Reeling
3.29K10 -
 DVR
DVR
Outspoken with Dr. Naomi Wolf
1 hour ago"October 7: Israel, with all its Flaws, isn't Making me a Zionist. Anti-Semitism Is."
1.3K6
