Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
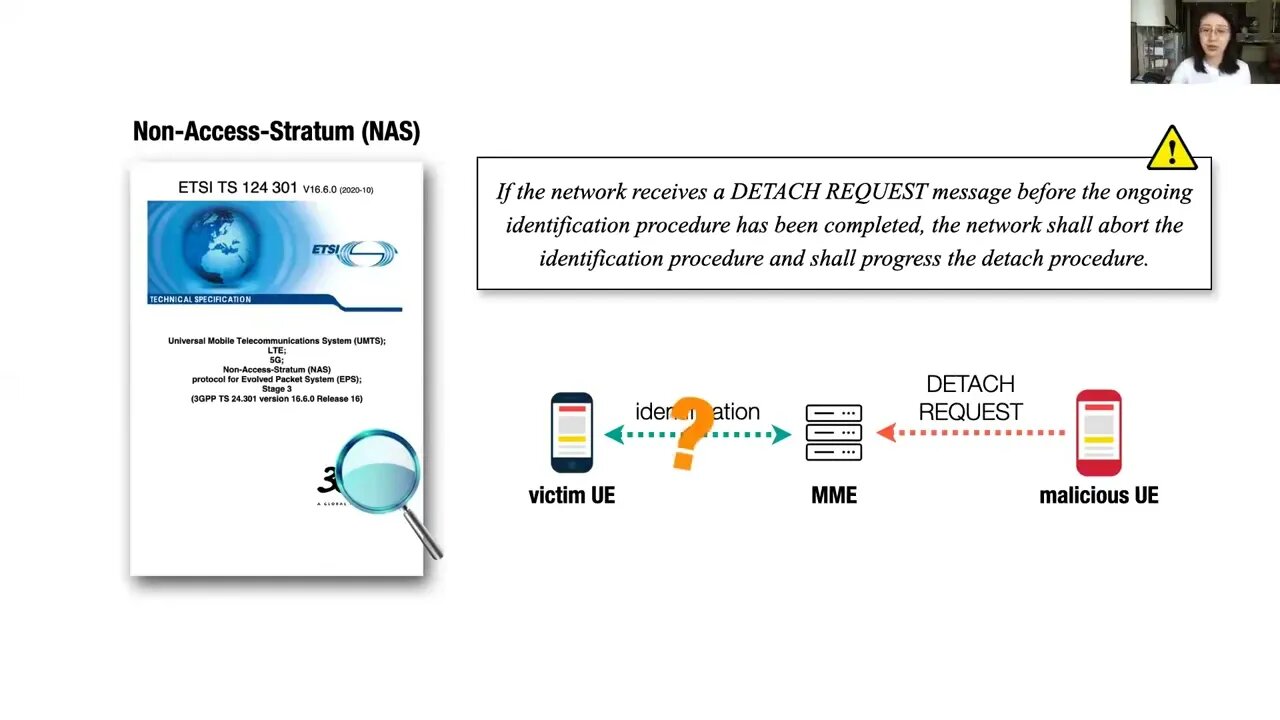
Bookworm Game Automatic Discovery of LTE Vulnerabilities Through Documentation Analysis
Loading comments...
-
 27:49
27:49
Jasmin Laine
18 hours agoDanielle Smith WARNS: “A Decade Of LIES”—U.S. Fallout Backfires BADLY
42.6K30 -
 3:39:58
3:39:58
Joe Donuts Live
3 hours ago🟢 Black Ops 7 AR Grind Begins | Dropzone Sundays
11.2K -
 LIVE
LIVE
Reidboyy
18 hours ago $3.00 earned24/7 BO7 Camo Grind! Stream Doesn't End Until I Unlock EVERY Camo in Black Ops 7!
260 watching -
 17:04
17:04
T-SPLY
18 hours agoCongresswoman DENIED By Judge To Drop Federal Assault Charges!
15K24 -
 3:01:07
3:01:07
Wahzdee
4 hours agoTHE "I WON'T QUIT" STREAM... FAILED | Tarkov 1.0 Broke Me | Playing Liar's Bar
15.3K4 -
 10:46
10:46
China Uncensored
19 hours agoHasan Piker Finds Out the Hard Way...
21.9K22 -
 59:40
59:40
American Thought Leaders
16 hours agoHe Said No to Billions from China. Now They’re After Him | Declan Ganley
21.7K10 -
 4:58
4:58
GreenMan Studio
15 hours agoTHE RUMBLE COLLAB SHOW EP.4 W/Greenman Reports
16.9K4 -
 8:05
8:05
Freedom Frontline
18 hours agoAOC DISRESPECTS Byron Donalds And Gets DESTROYED Immediately
14.7K7 -
 11:53
11:53
GBGunsRumble
16 hours agoGBGuns Range Report 15NOV25
10.9K1