Premium Only Content
Cyber Security Training for Beginners - Full Course
In this Computer security course, we'll learn everything about Cyber Security. Cyber security is the application of technologies, processes and controls to protect systems, networks, programs, devices and data from cyber attacks.
This cybersecurity course is for beginners who would like to kickstart their cyber security career.
1 - Avoiding Plagiarism
A brief introduction to plagiarism. This video gives some tips for avoiding plagiarism of ideas and language.
2 - Why Study Cyber Security
Sketches some reasons why everyday people would want to study cyber security.
3 - Cyber Security Terminology
Presents new vocabulary terms in context with true stories about cyber attacks.
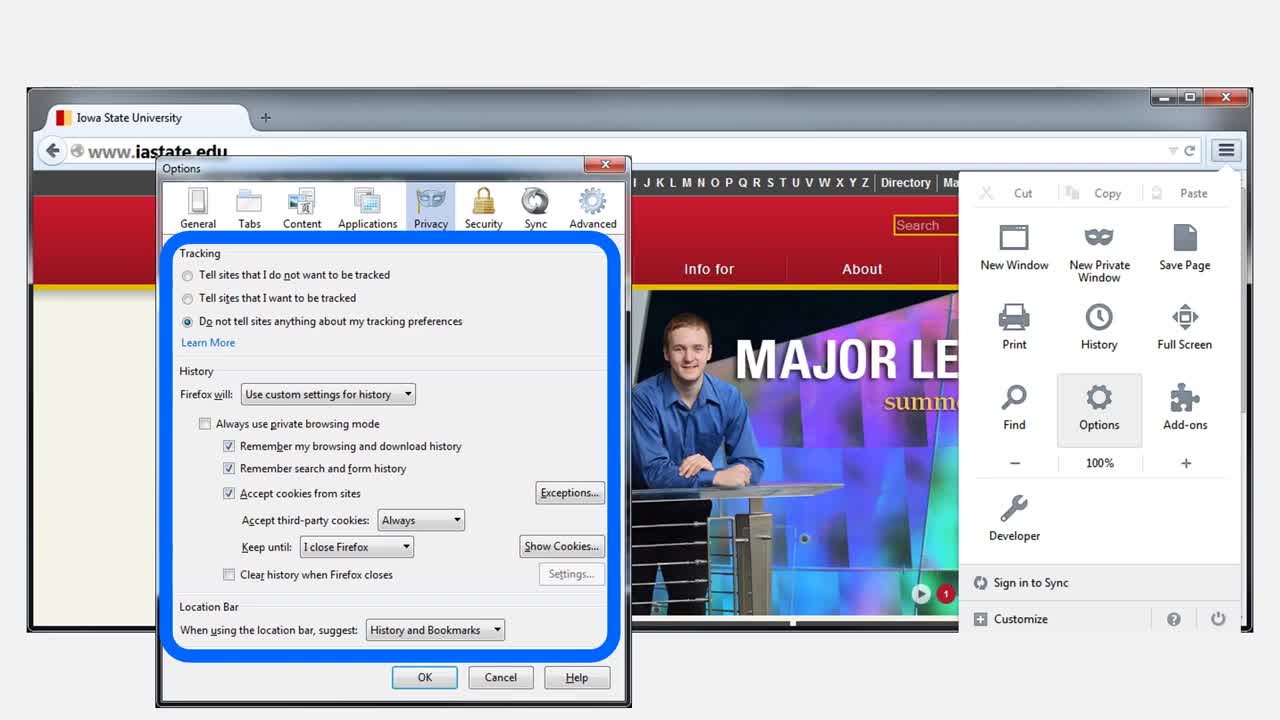
4 - Demystifying Computers
Identifies the basic parts of a computer in plain English. Describes four layers of a computer system: Users, Hardware, Operating System, Applications
Describes what happens when users turn on a computer and when they run an application.
5 - Demystifying the Internet
Introduces some helpful concepts for understanding the Internet.
Describes the basic structure of the whole Internet. Also describes the basic structure of small, individual networks like home wireless networks or office networks.
Describes how information is routed across the Internet.
6 - Passwords and Hash Functions
Discusses why passwords are so prevalent today and how organizations use hash functions to secure stored passwords.
7 - Common Password Threats
8 - Creating Strong Passwords
Provides tips for creating strong, memorable passwords.
9 - Managing Passwords
Provides tips for managing passwords
10 - How Email Works
Describes the paths that emails follow across the Internet.
11 - Email Security
Discusses six common email threats: Eavesdropping, Spamming and Phishing, Spoofing, Malicious Email Attachments, Replying and Forwarding Issues, Carbon Copy (CC) and Blind Carbon Copy (BCC) Issues
12 - Varieties of Malware
Introduces four different kinds of malware: Viruses, Worms, Trojan Horses, Bots
13 - Functions of Malware
Describes seven common functions of malware
14 - Sources of Malware
Describes eight common sources of malware
15 - Layers of Defense Against Malware
Describes five layers of defense against malware
16 - How Web Browsing works
An introduction explaining how computers interact with the web.
17 - Safely Navigating the Web
Discusses four web safety issues
18 - Online Shopping
Addresses eleven security issues for online shopping
19 - Wireless Network Basics
Provides a few brief notes on how wireless networks work.
20 - Wireless Internet Security Threats
Notice: We recommend that an adult screen this video before sharing it with young children. The fourth section of this video contains a passing reference to a serious and potentially frightening cyber crime.
21 - Using Public Wireless Networks
Shares five tips for safer browsing on public WiFi
22 - Administering Wireless Networks
Covers six tips for administering a home wireless network
23 - Social Media and Privacy
Addresses three privacy considerations for social media users
24 - Describes two security issues for users of social media: Burglars on Social Media, Phishing Scams and Malware on Social Media
25 - Social Engineering
Describes four common social engineering threats
26 - Reading URLs
Being able to read URLs helps web users to verify that they are visiting authentic web pages instead of malicious counterfeits.
27 - Interpersonal Issues Online
Describes five common interpersonal issues that web users should be aware of:
1. Anonymity
2. Missing the Communication Context
3. Privacy
4. Everlasting Information
5. Credibility
#CyberSecurity #Security #Morioh
PUBLICATION PERMISSIONS:
Original video was published with the Creative Commons Attribution license (reuse allowed).
Original video by IowaCyber
-
 30:00
30:00
BEK TV
3 days agoGUT HEALTH AND THE POWER OF KIMCHI WITH KIM BRIGHT ON TRENT ON THE LOOS
56K4 -
 LIVE
LIVE
IamNibz
9 hours ago $1.47 earned6-7 Minecraft Stream
177 watching -
 36:53
36:53
daniellesmithab
4 days agoSupporting Alberta's Teachers and Students
132K26 -
 1:25:28
1:25:28
VapinGamers
4 hours ago $1.95 earnedTools of the Trade - EP07 Lights, Camera, Go Live with Joker - !rumbot !music
27.2K5 -
 14:38
14:38
Nikko Ortiz
23 hours agoADHD vs Autism
96K51 -
 LIVE
LIVE
TonYGaMinG
4 hours ago🟢 INDUSTRIA 2 PLAYTEST / ACTIVE MATTER LATER
115 watching -
 2:43:39
2:43:39
FoeDubb
5 hours ago🏰KINGDOM MENU: 🎮SHORT SATURDAY SESH ON DECK DILLY DILLY!!
26.6K3 -
 2:09:04
2:09:04
GlizzyPrinceChristian
5 hours agoCOD SATURDAYS DIGGY DIGGY DIGGY| We Testing Out This Beta
18.5K2 -
 LIVE
LIVE
MrR4ger
7 hours agoSCARETOBER DAY 4 - AMNESIA: THE BUNKER - ACTIVE MATTER WITH GUMO AN TONY #PARTNERED STREAM
17 watching -
 6:29:28
6:29:28
FyrBorne
18 hours ago🔴Warzone/Black Ops 7 M&K Sniping: From the Zone to Zombs
34.4K1
