Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
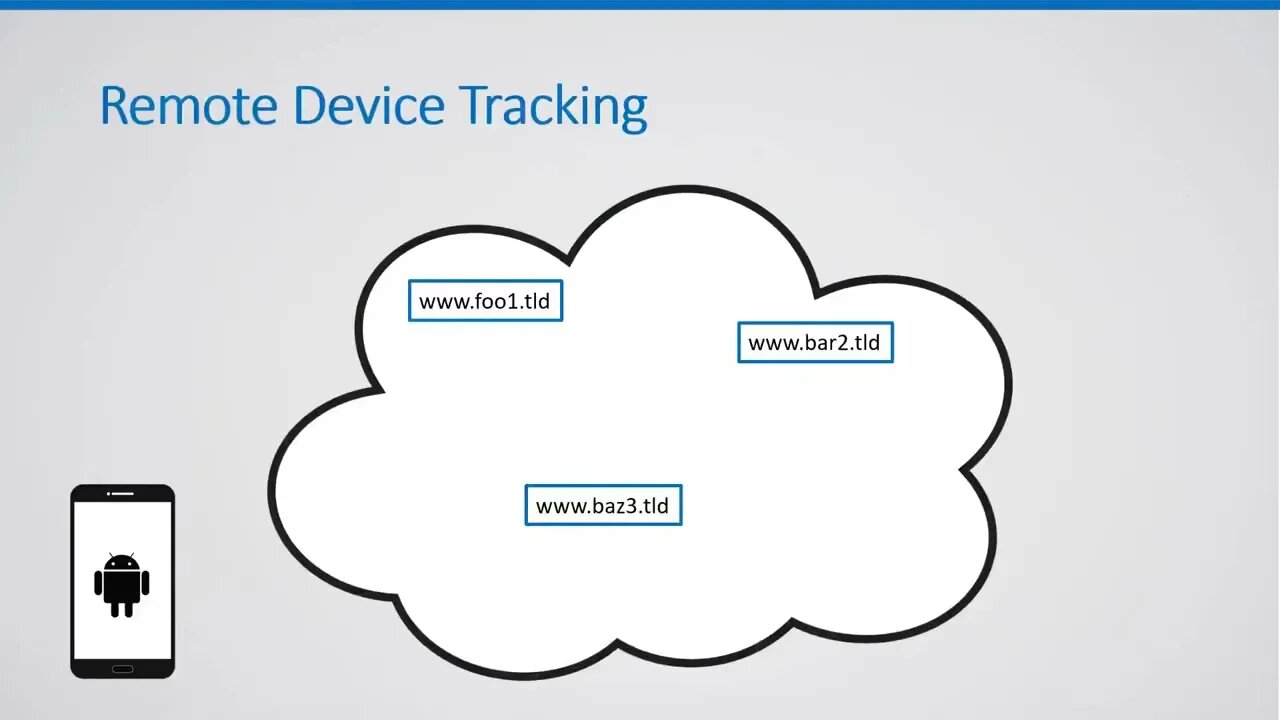
Cross Layer Attacks and How to Use Them for DNS Cache Poisoning, Device Tracking and More
Loading comments...
-
 1:35:03
1:35:03
Russell Brand
3 hours agoDemocrats Drop Epstein Emails — All About Trump - SF650
65K31 -
 LIVE
LIVE
Nerdrotic
2 hours agoBBC Crashout | Hollywood For Sale | Battle of the Blonde's | Witcher BOMBS - Friday Night Tights 380
1,308 watching -
 14:26
14:26
Upper Echelon Gamers
3 hours ago $0.13 earnedThe Carvana Scam - A Predatory BUBBLE
3.66K3 -
 LIVE
LIVE
LFA TV
20 hours agoLIVE & BREAKING NEWS! | FRIDAY 11/14/25
1,061 watching -
 LIVE
LIVE
Dr Disrespect
6 hours ago🔴LIVE - DR DISRESPECT - BLACK OPS 7 - LAUNCH DAY CHAMPION
1,158 watching -
 DVR
DVR
StoneMountain64
4 hours agoCall of Duty Black Ops 7 Gameplay LAUNCH DAY
34.8K -
 18:15
18:15
Clintonjaws
6 hours ago $3.25 earnedCNN Audience Shocked By Dem's Slanderous Comments At Trump
32.5K20 -
![MAHA News [11.14] - Govt War on Small Ranchers, GLP-1 Craze, Hemp Ban, Mercury out of Vaccines](https://1a-1791.com/video/fww1/f2/s8/1/i/X/E/z/iXEzz.0kob-small-MAHA-News-11.14.jpg) DVR
DVR
Badlands Media
12 hours agoMAHA News [11.14] - Govt War on Small Ranchers, GLP-1 Craze, Hemp Ban, Mercury out of Vaccines
19.9K3 -
 1:23:17
1:23:17
The Quartering
5 hours agoTucker Reveals FBI Coverup For Trump Assassin, Walmart CEO Quits & Tim Pool Unleashes
63.2K64 -
 34:23
34:23
Tucker Carlson
9 hours agoWho Is Thomas Crooks?
350K498